 CacheGuard-OS
CacheGuard-OSUser's Guide - Version UF-2.5.1
Network Security
CacheGuard appliance distinguishes between two types of network traffic: traffic exchanged with the appliance itself, and traffic that is only routed via the appliance (for which the source or destination is not the appliance itself). To control the traffic exchanged with the appliance, you can use the access command, while the firewall command can be used to control routed traffic. Both types of traffic are managed by a stateful firewall integrated into the appliance.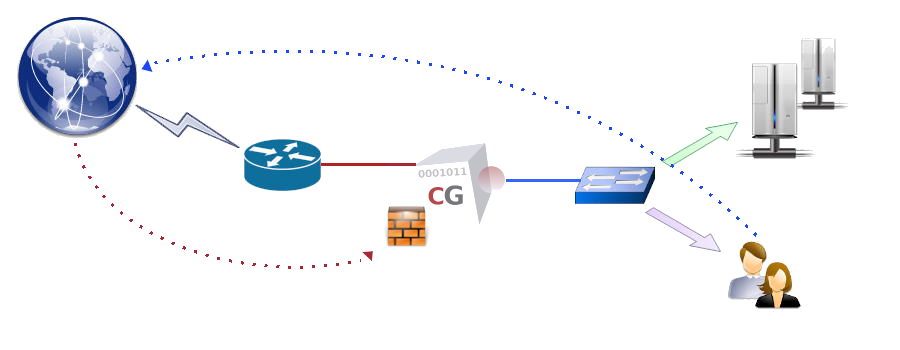
Administration Access
For security reasons, administration access (via SSH or the Web GUI) to a CacheGuard appliance is granted only to users or machines located within trusted networks. The same rule applies to file servers and monitoring systems that need to access the appliance. File servers are used to exchange files (via TFTP, FTP, or SSH) with the appliance for configuration or administration purposes (for instance, to load or save SSL certificates or perform a system backup). Monitoring managers can be used to monitor the appliance using SNMP.In the example below, the appliance is configured to allow SSH and Web administration GUI access via its internal network interface to remote users or machines in the 172.18.2.0 255.255.255.0 network. In addition, the SNMP manager with the IP address 172.18.2.202 is authorised to send SNMP requests to the appliance via its internal network interface, and the file server ftp.cacheguard.net is authorised to exchange files with the appliance via its external network interface.
- access admin add internal 172.18.2.0 255.255.255.0
- access file add external ftp.cacheguard.net
- access mon add internal 172.18.2.202
- apply
- password file add ftp ftp.cacheguard.net john
- access file add internal 172.18.2.203 sftp john
- apply
Web Browsing Access
By default, the Web proxy is accessible to all devices except those located in the external zone (routed via the external network interface). This default access policy can be modified using the access web command to restrict access to predefined networks only. To activate Web proxy access limitation, you must define at least one Web access rule. Note that when at least one previous peer or transparent network is defined, access limitation is implicitly activated, and you must explicitly specify permitted networks. Refer to the peer and transparent command manuals for more information about peers and transparent networks.To restrict Web proxy access to devices located in the 172.18.2.0 255.255.255.0 and 10.26.0.0 255.255.0.0 networks via the appliance’s internal network interface, use the following commands:
- access web raz
- access web add internal 172.18.2.0 255.255.255.0
- access web add internal 10.26.0.0 255.255.0.0
- apply
The Firewall
CacheGuard appliance can act as a stateful firewall with NAT capabilities to filter routed network traffic according to source and destination IP addresses and protocols. To filter network traffic, you must define firewall rules. A firewall rule is attached to a network interface and controls incoming traffic through that interface. Rules attached to a network interface form a rule set, and there is one rule set per interface. To use the firewall, you must first activate it using the mode firewall on command and then define rules using the firewall command. In the absence of any rules, the following default rules are applied:- New connections incoming from the external zone and destined for the internal, auxiliary, and vpnipsec zones are denied.
- New connections incoming from the internal zone (the web zone in VLAN mode) and destined for other zones are permitted.
- New connections incoming from the auxiliary zone are denied by default. To allow such traffic, you must explicitly define rules.
- In VLAN mode (mode vlan on), new connections incoming from the rweb, antivirus, admin, mon, file, and peer zones are denied by default. In non-VLAN mode (mode vlan off), these are all considered part of the internal zone and therefore follow its rules.
- New connections incoming from the vpnipsec zone and destined for the internal zone (the web zone in VLAN mode) are permitted. Connections incoming from the vpnipsec zone and destined for other zones are denied by default.
- mode firewall on
- mode router on
- firewall web add allTCPToInternet allow tcp 172.18.2.0/24 external
- apply
When defining a firewall rule, you may also apply NAT (Network Address Translation) to the source and/or destination IP addresses of the traffic. For example, the following commands allow the IP address 192.168.44.55 to establish TCP connections via the external interface to the destination 192.168.22.11:80 and translate that destination to 10.0.10.11:81:
- mode firewall on
- mode router on
- firewall external add allWeb allow tcp 192.168.44.55 admin 192.168.22.11 80 nil 10.0.10.11 81
- apply
IPsec VPN
VPN stands for Virtual Private Network, and IPsec for Internet Protocol Security. An IPsec VPN allows you to authenticate and encrypt data packets between private networks over a public IP network (for instance, the Internet) to provide secure encrypted communication. You can create persistent IPsec VPNs between sites or enable remote workers to access your internal infrastructure securely via an IPsec VPN. CacheGuard appliance integrates an IPsec VPN server that you can activate using the mode vpnipsec on command. The vpnipsec command is then used to configure the IPsec VPN server.
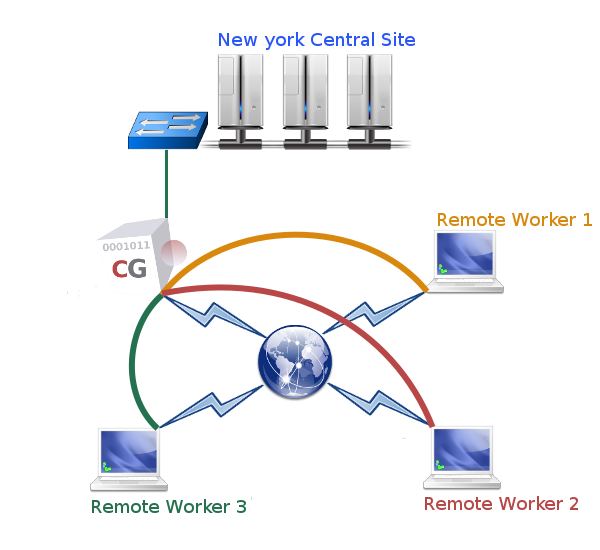 Two types of IPsec VPNs are supported: site-to-site VPNs and remote-access VPNs. A site-to-site (or inter-site) VPN enables a permanent secure tunnel between two sites, allowing computers in both locations to communicate securely as if they were in the same place. To establish such a VPN tunnel, you require two VPN servers: a local VPN server and a remote (peer) VPN server.
Two types of IPsec VPNs are supported: site-to-site VPNs and remote-access VPNs. A site-to-site (or inter-site) VPN enables a permanent secure tunnel between two sites, allowing computers in both locations to communicate securely as if they were in the same place. To establish such a VPN tunnel, you require two VPN servers: a local VPN server and a remote (peer) VPN server.
A remote-access VPN enables remote users to connect securely to a central VPN server. Such tunnels allow remote workers to access systems protected by the VPN server securely, as if they were physically connected to the internal network.
Please note that on a CacheGuard appliance, you must choose between site-to-site mode or remote-access mode; both cannot be activated simultaneously. The vpnipsec access on and vpnipsec access off commands enable you to switch between modes.